Categories
Effective Online Learning
As the educational and professional community moves to e-learning, CYRIN provides a best in class experience for a live interactive cyber range with up to four different levels of training. CYRIN has a growing catalog of cyber defense training labs in critical areas for Educators, Students and Professionals.
CYRIN has three Levels - Labs, Exercises, and Attack Scenarios. These are completed in progression. Coming in 2020 is a new level called Level 4. Developed by a world-renowned cyber trainer, Level 4 consists of three courses with immersive week-long training for each course.
LEVEL 1: SKILLS DEVELOPMENT LABS, 34+ instructional labs in eight categories
- Secure Network Setup
- Secure System Setup
- Network Monitoring & Recon
- Vulnerability Scanning
- Secure Web Application Setup
- Web Application Security Analysis
- Incident Response
- Cyber Forensics
ATCorp publishes at least one new cybersecurity lab per quarter.
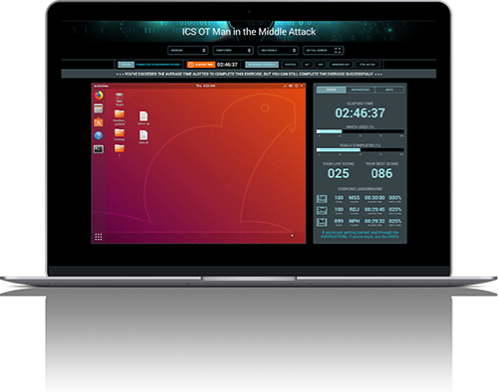
LEVEL 2: EXERCISES
After Labs, Level 2 Exercises are the next step where students and professionals are tasked with actual exercises; many of these will or can be done in a team atmosphere – red team, blue team – offense vs. defense.
- Teams can unleash their tools and knowledge to destroy targets of varying difficulty and threat level, or have them compete head-to-head in attack/defend war games.
- Red/blue exercises test everyone’s abilities with virtual capture-the-flag, defacement and denial of service scenarios.
- CYRIN provides forensic exercises using representative enterprise networks.
ATCorp publishes at least one new exercise per quarter.
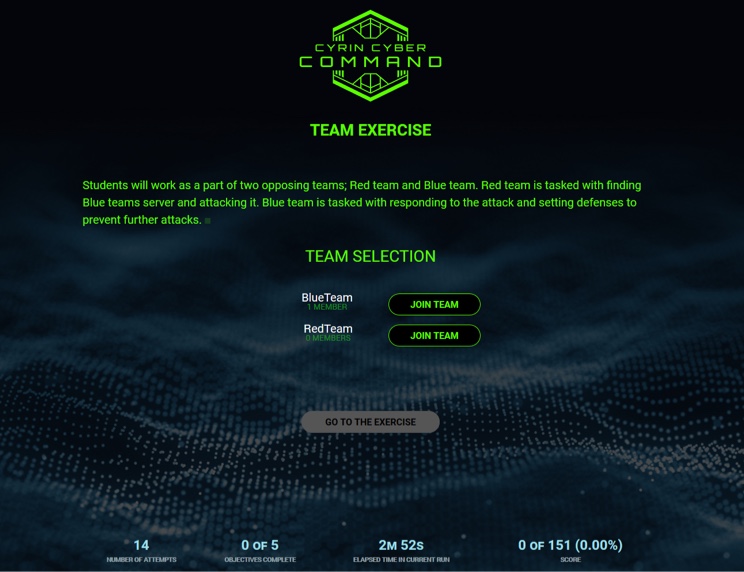
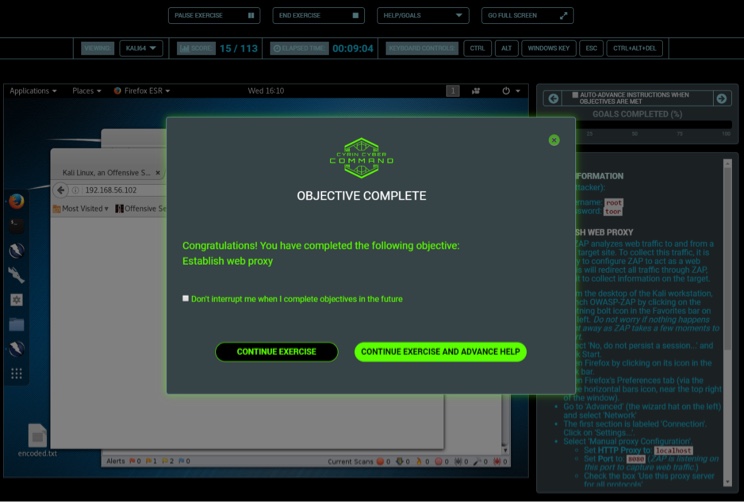
LEVEL 3: ATTACK SCENARIOS
This level requires the student to apply what they’ve learned in Levels 1 and 2. Level 3 presents more robust challenges where the student needs to think on their feet to ascertain the source of the attacks.
Current Attack Scenarios
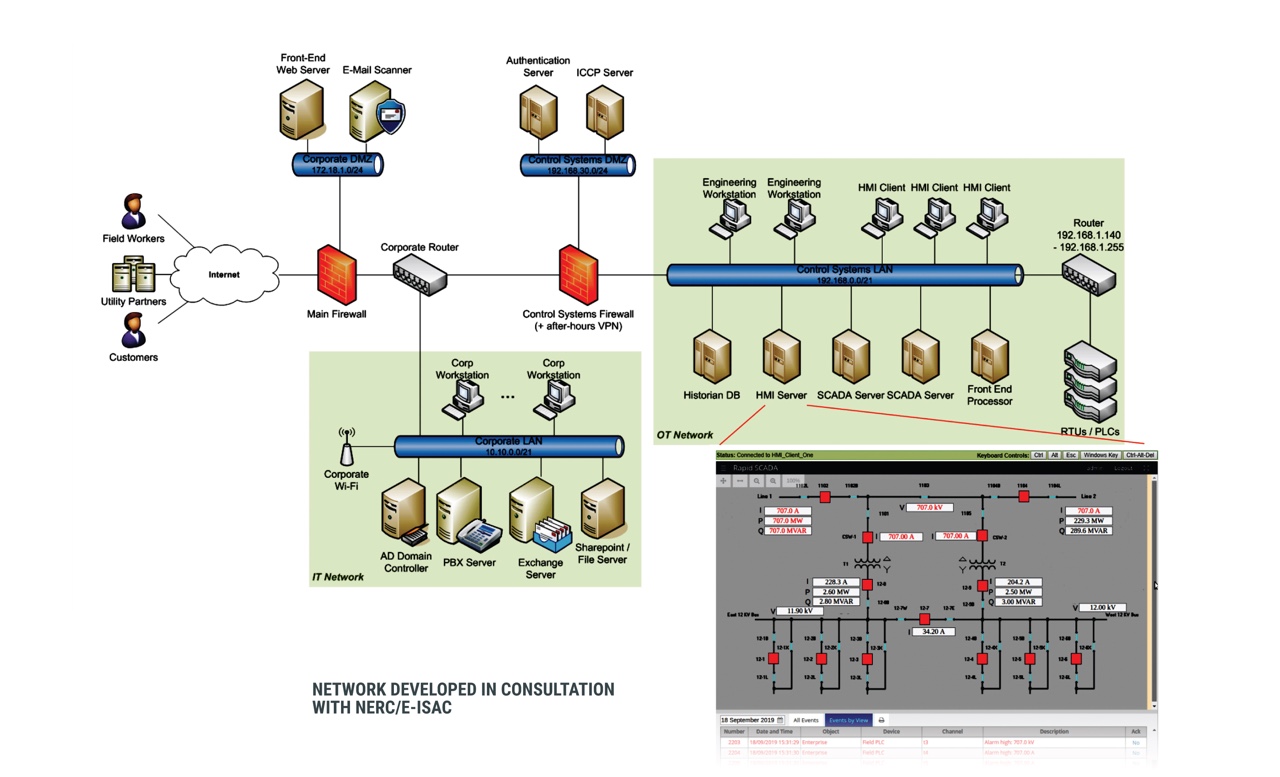
- Realistic, vendor-agnostic enterprise and operational/SCADA networks with background traffic for added realism.
- Unauthorized modification of PLC registers via Modbus, e.g., to trip breakers (akin to Stuxnet).
- DoS against PLCs that have connection limits; makes SCADA “blind” as to what’s going on.
- Man in the Middle between PLC and SCADA, causing wrong information to be displayed/used (e.g., as in a supply chain compromise).
- Phishing email that scans the ICS network and sends bogus Modbus data.
- Exfiltrate PLC/Modbus data for recon purposes (similar to Havex).
ATCorp publishes at least one new attack scenario per quarter.
LEVEL 4: COURSES (available later in 2020)
Level 4 will have three separate modules. Each module is a week-long course with 10-15 labs. Students will advance from the first course to the third.
1. Cyber Security Skills Foundation
- Learn the essential skills to build a solid security foundation.
- CYRIN students will examine in detail the traffic that traverses the network at the packet and binary level.
- Students will build a solid knowledge of the lowest layers of the network.
- This course offers extensive hands-on exercises.
- Students will learn how to master the TCP/IP protocol.
- Students will learn the essential UNIX and Linux survival skills that will separate them from the crowd of security professionals who are Windows-centric.
- Students will be introduced to vulnerability assessment and the hacking methodology.
- Upon course completion, students will have a solid security foundation to pursue more advanced security training.
2. Essential Defense Tactics
- CYRIN students experience hands-on training and learn the foundation of security and defending architectures from attack.
- Students will study the mindset of “thinking like a hacker” to learn techniques to defend against attacks that are commonly conducted against the IT corporate networks as well as industrial control networks.
- Students will learn powerful methods to analyze the risk of both the IT and corporate networks. Once set in their foundation knowledge, students will study best-practice recommendations when it comes to reducing the attack surface.
- Students will learn a systematic process of intrusion and malware analysis.
- This intensive course will introduce attacks that ultimately compromise systems and networks. Students will then design defensive mechanisms to prevent the attack or isolate the attack if prevention is not possible.
3. Advanced Defense
- CYRIN students are among the few who will transcend the old idea of the hacker having all the fun.
- Take pride in being the defender, form an offensive mindset to orchestrate robust and reliable defenses skillfully, and defy popular belief by beating the hacker at their own game.
- Students will evaluate advanced hacking methods of defense fortification, bringing you closer to establishing perfect security best practices and methodologies you can apply to secure environments.
- This course provides segmentation and isolation to reduce the effectiveness of advanced persistent threats.
- This course covers fundamental areas of fortifying your defenses.
- Students will discover methods of developing a secure baseline and learn how to harden your enterprise architecture from the most advanced attacks.
- Once a strategy for a fortified perimeter is defined, the course moves on to defend against the sophisticated malware on the rise today and reinforces the importance of live memory analysis and real-time monitoring.

Current Labs, Exercises, and Attack Scenarios
Networks

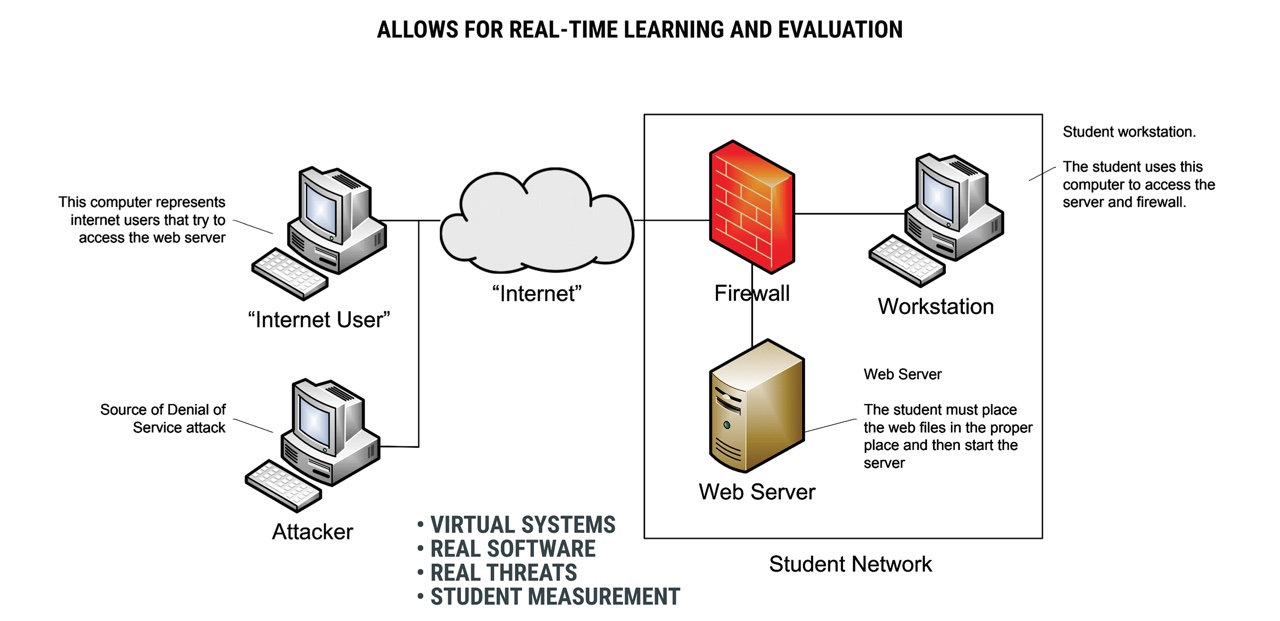
Sample Training Network

Sample ICS Scenario Network

Current Labs, Exercises, and Attack Scenarios
Resources
Automated Performance Monitor
and Exercise Builder
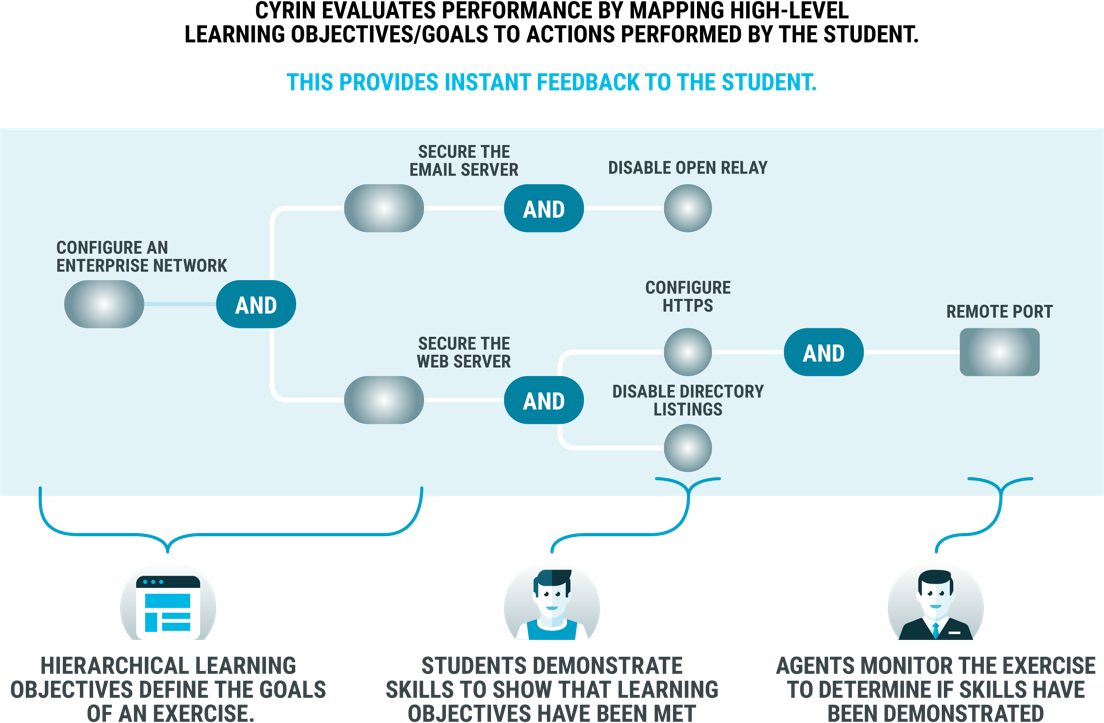
- Both CYRIN students and instructors can evaluate their performance via the automated performance monitoring module by mapping high-level learning objectives and goals to actions performed by the student.
- Instant feedback for the student allows educators to look at the performance of one student or visually map the whole class and append grade levels or points to each student.
- Exercise Builder allows educators to build new labs and new courses into the CYRIN training platform.
- Exercise Builder will let you move from idea to lab in hours.

Automated Performance Monitoring
Exercise Builder Module (EBM)
- Exercise Builder allows you to build new labs and new courses into the CYRIN training platform.
- Exercise Builder lets you move from idea to lab in hours.
- Exercise Builder is flexible and can be tailored to many types of courses, not just cybersecurity.
- The Exercise Builder allows CYRIN training to support the current generation of cybersecurity professionals while developing the next generation of cybersecurity leaders.